Proactive Security by Design
Beacen vSeries eliminates threats — not just reports them.
Unlike traditional security models that react after a breach, BeacenAI’s vSeries platform is architected for proactive defense, eliminating attack surfaces before they can be exploited.
At its core, zStation flips the script: it’s not about containing threats — it’s about never exposing the surface to attack in the first place.
No Surface, No Entry
Every zStation boots stateless and runs completely in volatile memory. There’s no writable filesystem, no persistent apps, no configuration files to hijack. Combined with zero local storage and read-only OS execution, zStation endpoints are invisible to common malware tactics.
Integrated SDN Security — Right to the Edge
Each zStation endpoint includes an Open 64-port virtual switch (vSwitch), extending Software-Defined Network (SDN) security policies all the way to the edge. This means
- Per-application traffic segmentation
- Enforced microsegmentation from core to endpoint
- Full compatibility with data center-grade policies
- Real-time flow control based on identity and context
Network security isn’t just centralized — it’s everywhere.
Application-Level Containment
Beacen vSeries enforces strict application isolation using three layered technologies — ensuring that even if an application misbehaves, it’s fully sandboxed and contained.
1. Secure Sandbox
Each application runs with its own isolated memory heap and limited file access. No cross-talk, no unauthorized I/O, and no shared memory.
If it’s not explicitly allowed, it’s not accessible.
2. Secure Dock (Containers)
Lightweight, portable, containerized apps that run the same anywhere, regardless of the host device or OS.
Each container is fully self-contained and locked down — isolating software stacks and preventing environment-based attacks.
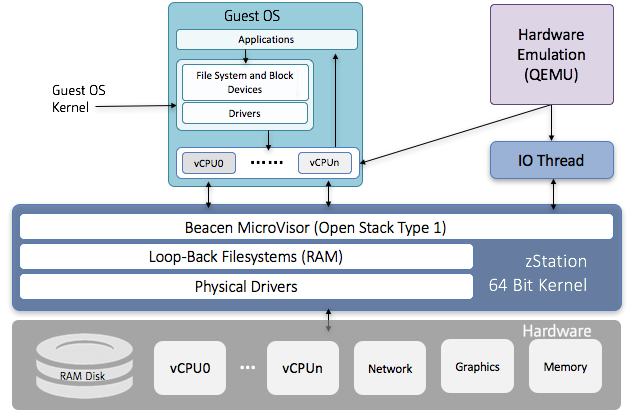
3. Secure Container (Hypervisor Mode)
For advanced use cases, zStation can act as a Type 1 hypervisor, supporting full guest VMs:
- Fully isolated from the zStation host
- Encrypted at rest with AES loop encryption
- Loaded via network or local secure cache
- Optional hardware passthrough or emulation mode
Ideal for regulated environments, legacy support, or total tenant isolation.
Security That’s Policy-Aware and AI-Enforced
Beacen’s AI-based policy engine determines how each endpoint is built, what services are allowed, and how data is routed — dynamically and in real time.
- Access is tightly controlled by identity, location, and role
- Policy changes take effect immediately at the edge
- No static rules, no stale configs — only live, intelligent enforcement
BeacenAI doesn’t detect threats — it eliminates the opportunity for them to exist.
Beacen vSeries Benefits
Plug-and-Play
Your computer becomes a true plug-and-play appliance, capable of working "out of the box" without the need for any administrative intervention. The installer only has to plug it in; and turn it on.
Fully Responsive
As technology continues its steady migration to mobile platforms it is not enough for the application to be the only responsive element. zStation’s modularity guarantees a completely responsive environment.
Secure
vSeries represents a new level of security, reducing if not eliminating attack vectors. Since the filesystem that the operating system resides on is read-only attachment points for viruses and malware simply don’t exist.
In-Memory
zStation endpoint operating environment operates exclusively in volatile RAM not requiring local storage for any operation. This architecture provides performance not attainable by traditional computer architectures.
Stateless
Remember when your computer was new, everything was fast and it just worked, as it gets older your computer seems slower, that’s because it is, operating system decay is a real issue. Since zStation is stateless it is new evry time you login.
Consistent
Policy based computing guarantees that the system is deployed in the ideal configuration. Both operating system and application workloads are always in the optimal configuration on all systems.